
Andreea Stanovici, December 12, 2021
Get the Best Solution for
Your Business Today!
Secret managers have become the go-to tool to avoid hard coding credentials in source code. Secret managers provide a centralized place to store sensitive data like database credentials and API keys. In Amazon Web Services (AWS) there are two services for storing secrets: AWS Secrets Manager and the Parameter Store. The key to this workflow is specific PowerShell modules that will allow you to script operations of AWS resources directly from the PowerShell command line. The cmdlets within these modules allow you to set parameters for your commands and specify the value to be extracted. Note that when attaching an EC2 IAM role to the EC2 instance, it must have permissions to access Secrets Manager or SSM for the parameter store in addition to Amazon’s Key Management Service (KMS) in order to decrypt the secrets. If the instance does not have these permissions, the API call will not succeed unless there is an access key or a set of credentials with proper permissions passed through the command attempting to retrieve the secret.
Table of Contents
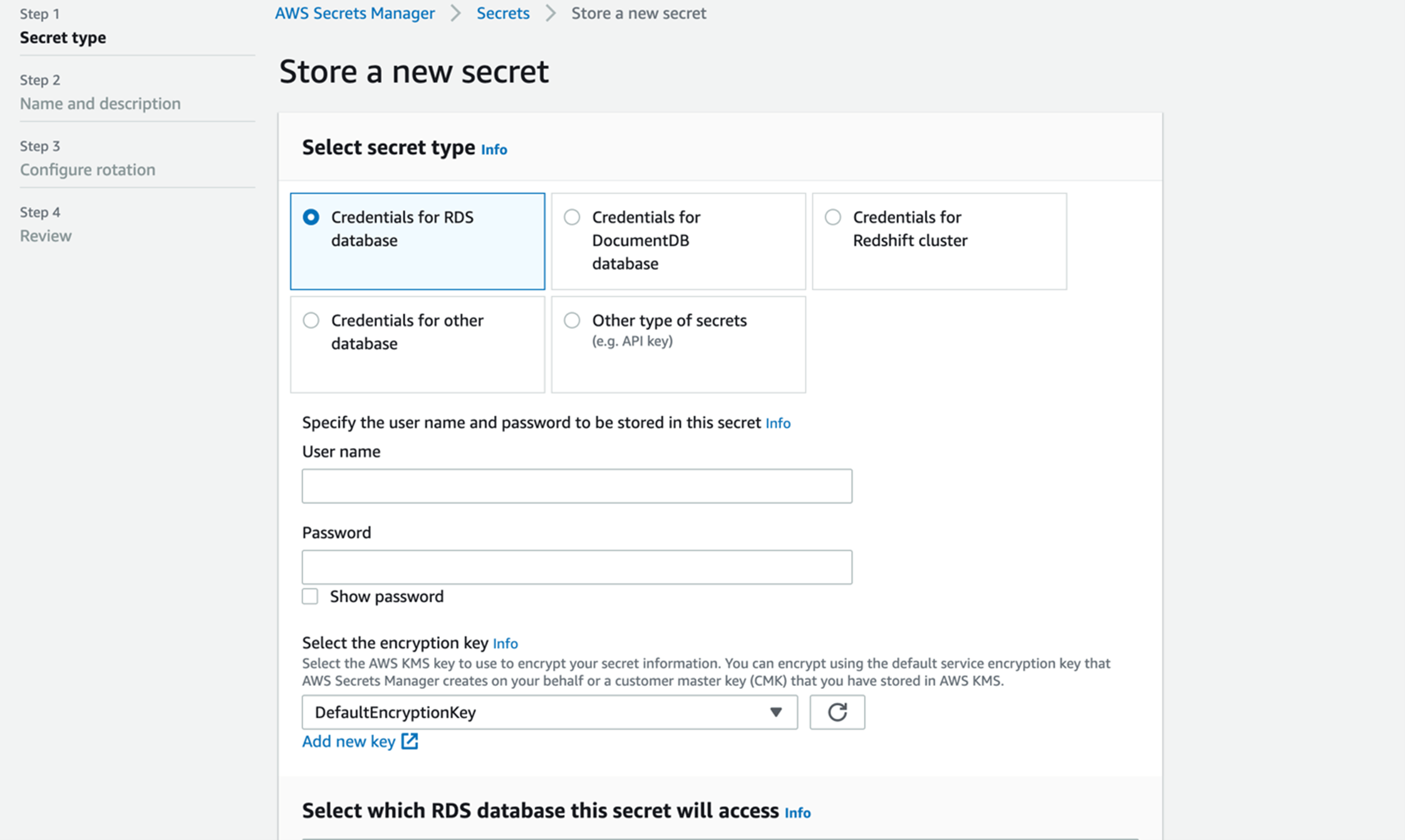
Secrets Manager – Preferred Method for Storing Sensitive Data
Secrets Manager is great for databases credentials and API keys. It can store both a username and password within the same secret. It is more expensive than the Parameter Store because it offers additional functionality including the rotation of keys, encryption by default, cross-region accessibility, and cross-account capabilities. The Secrets Manager console is very user friendly, and it groups the username and password together into a single secret, unlike the parameter store.
After you create an AWS secret, you will need to update your code to retrieve it. There is a piece of sample code that demonstrates how to retrieve the secret value, but the scripts are for Python3, Ruby, Java, JavaV2, JavaScript, C#, and Go as shown below.

AWS provides documentation for a variety of PowerShell cmdlets that can be used to make various API calls to the Secrets Manager. Some of these actions include creating, updating, and deleting secrets. The “Get-SECSecret” cmdlet Calls the AWS Secrets Manager DescribeSecret API operation. There are parameters that must be specified to retrieve the correct secret:
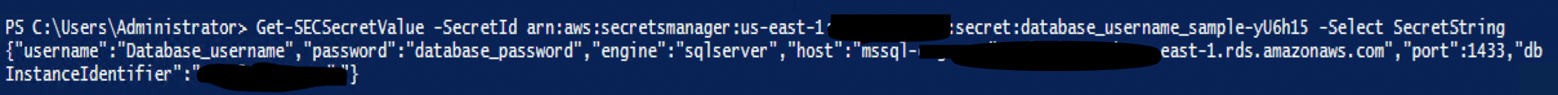
The “-SecretId” parameter specifies the exact secret being accessed. The value of the parameter would include the Amazon Resource Name (ARN). Using the command:
GET-SECSecretValue -SecretId arn:the_specific_arn_of_the_secret_being_retrievedwould produce the contents of the AWS secret in JSON format as shown below:
In order to select a specific property and have it converted from JSON to be passed through to a variable, there are a few more parameters and commands that would need to be included in the line. To retrieve just the username of the AWS secret in a plain text form, the command would look like this:
Get-SECSecretValue -SecretId arn:secret_arn_here -Select SecretString | ConvertFrom-Json | Select -ExpandProperty usernameSimilarly, to pass through just the password,
Get-SECSecretValue -SecretId arn:secret_arn_here -Select SecretString | ConvertFrom-Json | Select -ExpandProperty passwordSSM Parameter Store – Other Method for Storing Sensitive Data
Unlike Secrets Manager, the SSM Parameter Store can store only one value per AWS secret as shown below:

Each username would be stored in one secret, and its corresponding password would be stored in another secret. AWS does have documentation on retrieving secrets from the Parameter Store using the PowerShell CLI, however, this retrieves all of the details of the secret, not only the value. Retrieving a secure string secret from the Parameter Store in the PowerShell CLI would look like this:
Get-SSMParameter -Name “secret_name” -WithDecryption 1 | Select -ExpandProperty ‘Value’The “Get-SSMParameter” indicates you are trying to reach the parameter store, a feature of AWS Systems Manager. The “-Name” refers to the exact name of the parameter. The “-WithDecryption” assumes you are using a “SecureString” as is highly recommended. The last portion of the command filters the exact property of the secret that you are trying to retrieve. “Value” refers to the value of the secret that you would like to pass through. Without adding the last parameter, your secret would look like this:

Conclusion
The ability to print a single property of a secret regardless of secret location is crucial if you are trying to set the property value as a variable to be used throughout the script. This practice ensures that only the value itself would be passed through and the value itself would never be printed in plain text. If there was a security breach and the code was exposed, the users would not be able to access the content of the secret because the hackers would need proper permissions to make API calls to the AWS Secrets Manager or the SSM Parameter Store.
Next Steps
We hope you found this article informative. Be sure to subscribe to our newsletter for data and analytics news, updates, and insights delivered directly to your inbox.
If you have any questions or would like PMsquare to provide guidance and support for your analytics solution, contact us today.









